Hello there,
I’m proud to share a major development status update of XPipe, a connection hub and remote file manager that allows you to access your entire server infrastructure from your local machine. It works on top of your installed command-line programs and does not require any setup on your remote systems. So if you normally use CLI tools like ssh, docker, kubectl, etc. to connect to your servers, you can just use XPipe on top of that.
Here is how it looks like if you haven’t seen it before:
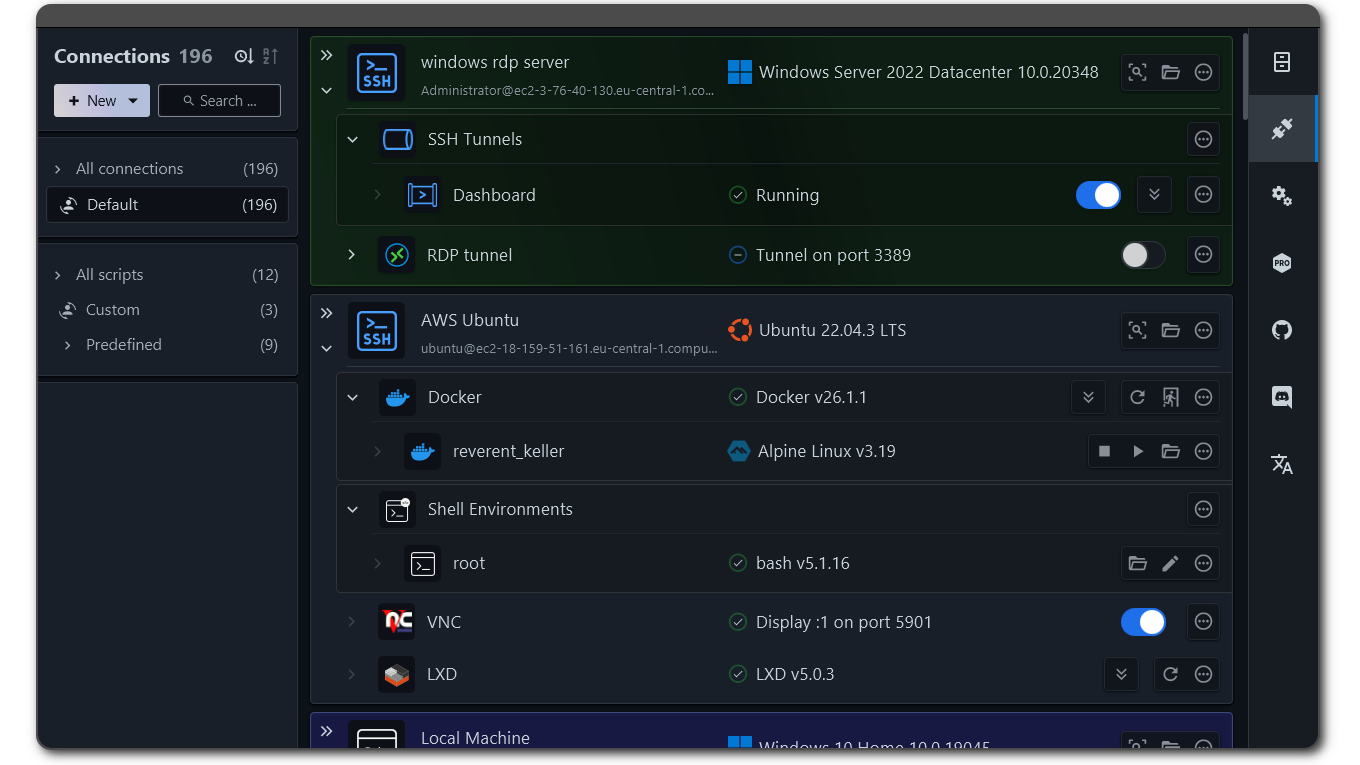
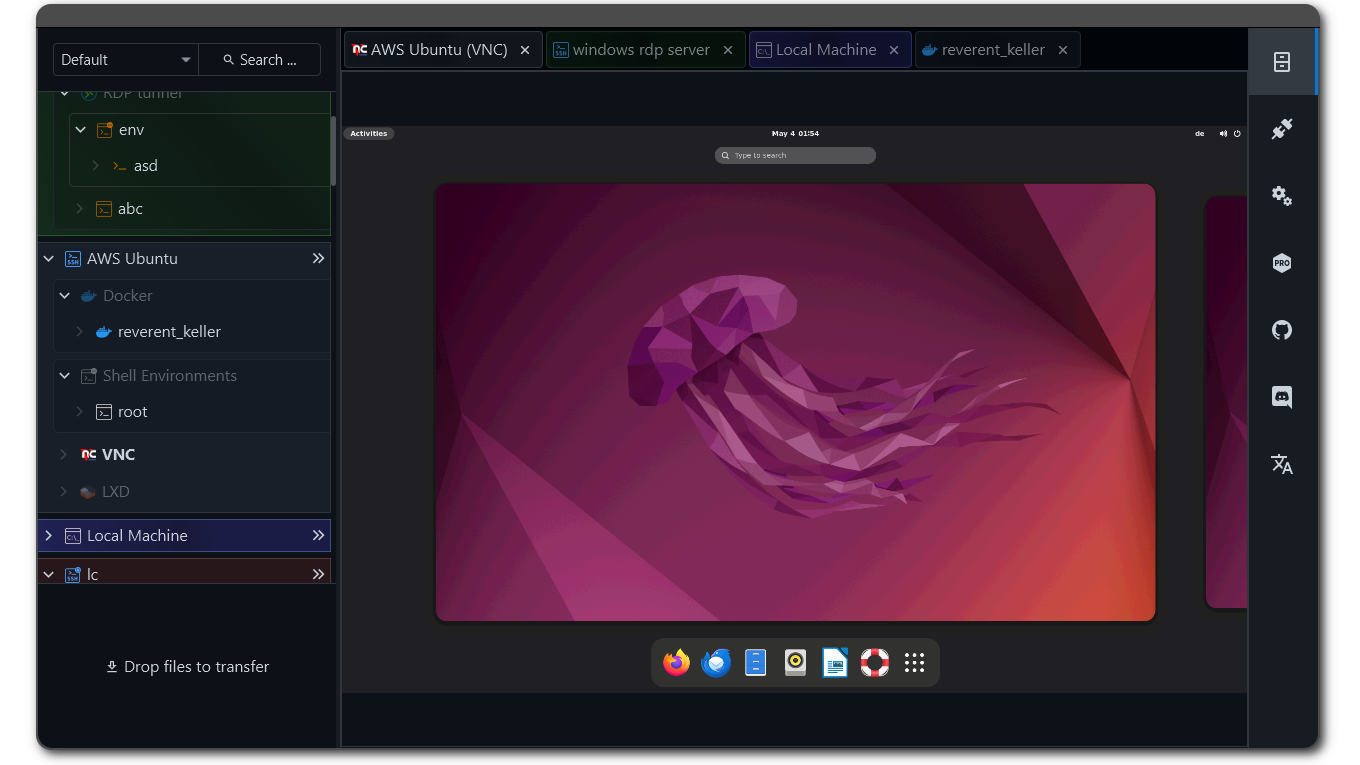
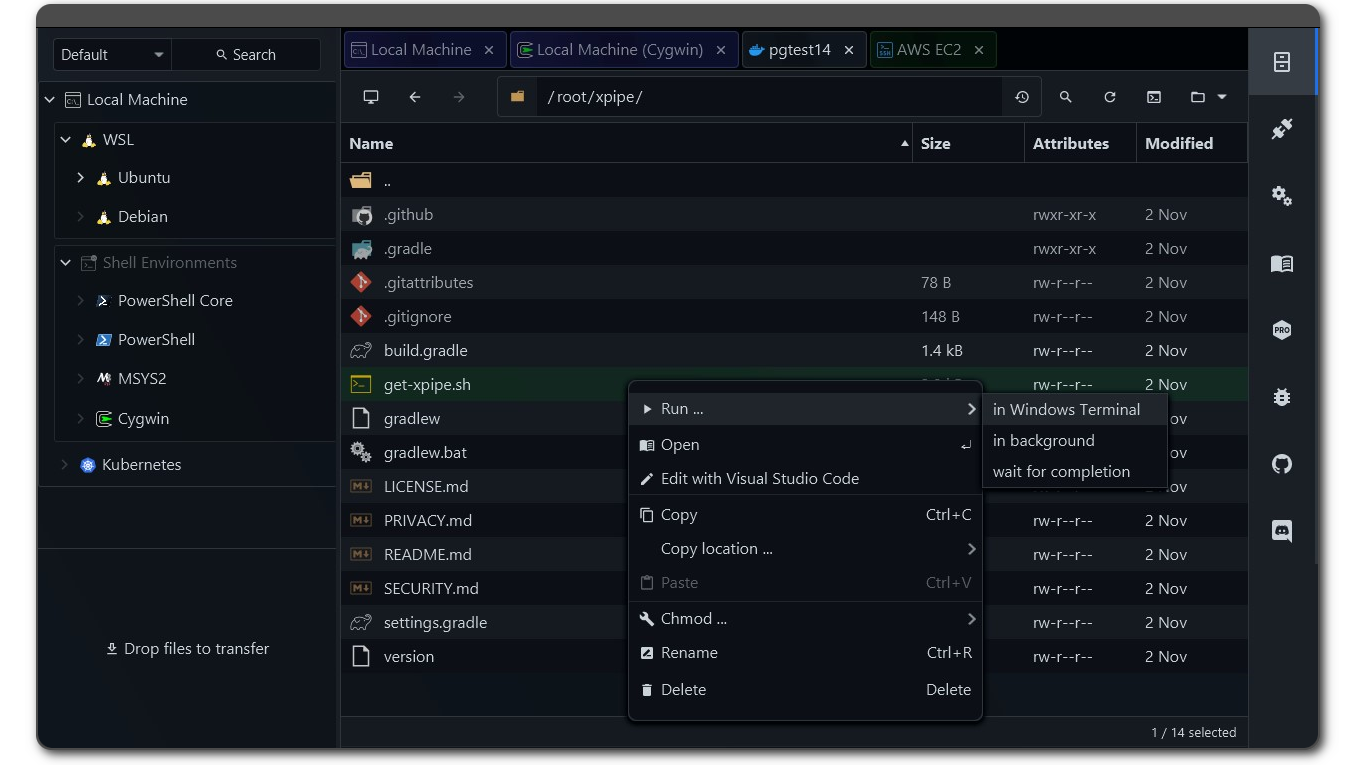
Coherent desktops
XPipe now comes with support for remote desktop connections. VNC connections are fully handled over SSH and can therefore be established on top of any existing SSH connection you have in XPipe. RDP support is realized similar to the terminal support, i.e., by launching your preferred RDP client with the connection information. X11-forwarding for SSH is also now supported.
With support for remote graphical desktop connection methods as well now in XPipe 9, the big picture idea is to implement the concept of coherent desktops. Essentially, you can launch predefined desktop applications, terminals, and scripts on any remote desktop connection, regardless of the underlying connection implementation. In combination with the improved SSH tunnel and background session support, you can launch graphical remote applications with one click in the same unified way for VNC over SSH connections, RDP connections, and X11-forwarded SSH connections.
SSH X11 Forwarding on Windows via WSL
You can now enable X11 forwarding for an SSH connection.
XPipe allows you to use the WSL2 X11 capabilities on Windows for your SSH connection. The only thing you need for this is a WSL2 distribution installed on your local system. XPipe will automatically choose a compatible installed distribution if possible, but you can also use another one in the settings menu.
This means that you don’t need to install a separate X11 server on Windows. However, if you are using one anyway, XPipe will detect that and use the currently running X11 server.
SSH connection improvements
-
All tunneled and X11-forwarded custom SSH connections are now properly detected and can be toggled on and off to run in the background
-
The connection establishment has been reworked to reduce the amount of double prompts, e.g. for smartcards or 2FA, where user input is required twice
-
The custom SSH connections now properly apply all configuration options of your user configuration file. They also now correctly apply multiple options for the same key correctly
-
Any value specified for the
RemoteCommandconfig option will now be properly applied when launching a terminal. This allows you to still use your preexisting init command setup, e.g. with tmux -
There is now support defining multiple host entries in place in a custom SSH connection. This is useful for cases where you want to use ProxyJump hosts in place without having to define them elsewhere
Terminal improvements
The terminal integrations have been reworked across the board. The kitty terminal is also now fully supported with tabs on both Linux and macOS. The Warp terminal integration now correctly enables all Warp features on remote shells. On macOS, other third-party prompts also now work properly in the launched terminals.
Password manager improvements
The password manager handling has been improved, and some potential sources of errors and confusion have been eliminated. There are also now a few command templates available for established password managers to quickly get started.
A note on the open-source model
Since it has come up a few times, in addition to the note in the git repository, I would like to clarify that XPipe is not fully FOSS software. The core that you can find on GitHub is Apache 2.0 licensed, but the distribution you download ships with closed-source extensions. There’s also a licensing system in place as I am trying to make a living out of this. I understand that this is a deal-breaker for some, so I wanted to give a heads-up.
The system is designed to allow for unlimited usage in non-commercial environments and only requires a license for more enterprise-level environments. This system is never going to be perfect as there is not a very clear separation in what kind of systems are used in, for example, homelabs and enterprises. But I try my best to give users as many free features as possible for their personal environments.
Outlook
So if you gave this project a try a while ago or it sounds interesting to you, you can check it out on GitHub! There are still more features to come in the near future. I also appreciate any kind of feedback to guide me in the right development direction. There is also a Discord for any sort of talking.
Enjoy!


It is a frontend for standard CLI tools yes, but it comes with many additional features. The focus is especially on integrating standard CLI tools with your desktop environment and other applications that you use like editors or terminals.
For example, of course you can just use the ssh CLI to connect to your server and edit files. But with XPipe you can do the same thing but more comfortably. You can source passwords from your local password manager CLI, automatically launch terminals with the SSH session, edit remote files with your locally installed text editor, and more.
Of course you can do this also with tools like putty, but the difference here is the integration. Other tools ship their own SSH client with its own capabilities, features, and limitations. They also have their own terminal. XPipe preserves full compatibility with your local SSH client and terminal. E.g. all your configuration options are properly applied, your configs are automatically sourced, any advanced authentication features like gpg keys, smartcards, etc. work out of the box.
The same approach is also used for the integrations for docker, podman, LXD, and more, so you can use it for a large variety of use cases.
So it’s a GUI, to a front-end of another tool, and it also introduces it’s own configurations into the mix? So like…building a bigger car around an existing car just to drive the smaller car. Not sure I’m really “getting it”. Like I don’t get why you’ve introduced a frontend to an existing GUI-based tool like a VNC or RDP viewer.
Edit: brutha, I’m getting downvoted exactly twice whenever I ask a question. It’s clearly OP. 🤦
RE: Your edit. Votes are public. OP didn’t downvote you. You, however, downvoted OP when they replied to your question. No idea why you’d do that when all they did was answer your question. FWIW I upvoted your comment so it doesn’t get buried, but yeah, people shouldn’t be downvoting posts unless they’re off topic or against the rules IMO. No need to weaponize them.
Yeah I did not downvote you, feel free to take a dive into the data if you really care about that.
I think your analogy about the cars can be augmented a bit. I would say that individual components like VNC are not really a car to begin with. VNC is an insecure protocol by default. Technically there are VNC security measures to potentially encode the data, but these are often not used*. Furthermore, even if you encrypt the data stream, VNC authentication options are severely limited. So something like VNC needs to run over something like a SSH tunnel to be considered properly secure. And to properly do that, you need an SSH integration as well. That is one example where these synergies happen in XPipe.
the point is to have all of the tools in one view.
And not to only aggregate them in one view but to also make them interact with each other. It’s not just about having SSH connections, docker containers, or VNC connections side by side, but using them together. For example, any VNC connection in XPipe is automatically tunneled over SSH, so you don’t even need to expose the port. If you add a system in XPipe via SSH, you will automatically have access to a VNC connection as well if a VNC server is running on it. Doing all of that manually is definitely possible, but will take you some time to set up and start each time.