Hey there folks,
I’m trying to figure out how to configure my UFW, and I’m just not sure where to start. What can I do to see the intetnet traffic from individual apps so I can know what I might want to block? This is just my personal computer and I’m a total newbie to configuring firewalls so I’m just not sure how to go about it. Most online guides seem to assume one already knows what they want to block but I don’t even know how/where to monitor local traffic to figure out what I can/should consider blocking.
You’ve got it backwards. A firewall blocks everything, then you open up the ports you want to use. A standard config would allow everything going out, and block everything coming in (unless you initiated that connection, then it is allowed).
So the question you should be asking, is what services do you think you’re going to be running on your desktop that you plan to allow anyone on the internet to get to?
Not entirely clear but perhaps OP is talking about blocking unwanted outgoing reqjests? E.g. anti-features and such since they mention traffic from their apps.
Possibly? The way I read it, it sounded like OP wasn’t really even sure what a firewall does.
no, not really. on linux that depends on the default policy of the corresponding chains, so it’s configurable. I don’t think all common distros default to reject either.
@Shdwdrgn @Cornflake_Dog false. a firewall can indeed have a default block everything policy, but this is still a configurable option
Sure it CAN be configured, but the typical policy of firewalls is to start from a position of blocking everything. From what I’ve seen, on Linux the standard starting point is blocking all incoming and allowing all outgoing. On Windows the default seems to be blocking everything in both directions. Sure you could start with a policy of allowing everything and block only selected ports, but what good is that when you can’t predict what ports an attacker might come from?
@Shdwdrgn on Linux, the firewall with zero custom rules always allowed everything. did that change in very recent kernels? if that’s the case, I’d expect a lot of lost acces to remote servers
Most of my experience is with iptables, but yeah, I think until you start adding rules nothing is implicitly denied? Once you enable a couple of initial rules then you should have good blocking from the outside while allowing internal traffic to connect freely. It doesn’t get in your way until you start using it, but then it doesn’t take much to get it going.
Please stop giving bad advise. The local firewall is not the same as the public firewall and nat on the router. Your comment is incredibly misleading. You can have no Firewall and the services will not be available publicly
What are you talking about? You’re assuming that every residential router is going to have some kind of firewall enabled by default (they don’t). Sure, if OP has a router that provides a basic firewall type service then it will likely block all incoming unauthorized traffic. However OP is specifically talking about a linux-based firewall and hasn’t specified if they have a router-based firewall service in place as well so we can only provide info on the firewall they specified. And if you look at UFW, the default configuration is to allow outgoing traffic and block all but a very few defined incoming ports.
You’re also making the assumption that OP is using NAT, when that is not always the case for all ISPs. Some are really annoying with their setup in that they give a routable IP to the first computer that connects and don’t allow any other connections (I had that setup once with Comcast). In this case, you wouldn’t even need to define port-forwarding to get directly to OP’s computer – and any services they might be running. This particular scenario is especially dangerous for home computers and I really hope no legitimate ISP is still following a practice like this, however I don’t take anything for granted.
Regardless of what other equipment OP has, UFW is going to provide FAR better defaults and configurability when compared to a residential router that is simply set up to create the fewest support calls to their ISP.
You know enough to be dangerous…
Why would an ISP assign a public IP to a users device? That wouldn’t make any sense. IPs are rare and expensive so that wouldn’t waste it on you. Each customer gets one IP and that is shared for all devices via NAT.
What your describing doesn’t make any sense
You’re right, it doesn’t make any sense. And it didn’t make any sense at the time either. After setting up the router with a laptop, I moved the connection to the firewall but it refused to connect. When I finally got ahold of tech support they said the connection locks into the first machine that logs in and they had to release it so I could connect the new machine. And just like that the firewall was given a routable IP address and connected to the internet. Stupidest thing I ever heard of, but that’s how they were set up. Now this was around 15+ years ago and I would certainly hope nobody is doing that crap today, but apparently that was their brilliant method of limiting how many devices could get online at once.
So some obscure thing you experienced 10 years ago is now the standard? I have been doing this a while and what you are describing is Franky crazy and I’ve never scene it outside of some business plans with bring your own device.
Who said anything about it being standard? I said I know this CAN happen, and I said it was quite some time ago. We can only hope this insanity isn’t still in practice anywhere, but I learned long ago that expecting a corporation to NOT do foolish things will give me the same disappointing results as expecting money to come out of my ass. If there’s a manager involved, then something on the tech side is going to get fucked up in the name of saving a buck. Therefore I cannot just assume OP gets a normal NAT address, nor can I assume they have any other firewall type device between them and the internet. With limited data, the best I can do is try and provide some general information, hopefully encourage them to ask more questions or provide more specific information, and just hope they don’t have a ridiculously stupid ISP that makes things needlessly complicated.
I fail to see why this is bad advice. Sure you could just disable the firewall on your computer on a local network. But that’s under the assumption that you can trust everything on your local network. What if it’s a laptop? Do you also trust any public networks you may connect to on the go? Having firewall both on the router and on your computer provides an additional layer of security, and I think that’s good advice in general. You can for example set it up to only allow incoming connections when connected to your home network for example.
There is a difference between good practice and fear mongering. You aren’t going to lose it all because you didn’t turn on the Firewall.
To be fair I haven’t configured a firewall either on my laptop. But that’s out of lazyness, not out of good practice. Good practice would be to have a firewall enabled. Just because something is unlikely to happen statistically doesn’t mean it’s bad practice to take steps to protect against it.
By default it should be configured to allow all outgoing, and block all incoming. That’s perfectly fine for a desktop/laptop and you don’t need to mess with it.
You can’t really do that much outgoing filtering with a firewall that will be useful, because basically everything operates on port 80/443, and often connects to the same CDNs or datacenter IPs for multiple services.
Instead DNS blocking is a much more effective way to handle it, plus uBlock Origin in your browser.
Just to clarify this comment for other “total newbies”: yes, the UFW default config is fine and “you don’t need to mess with it”.
But by default UFW itself is not even enabled on any desktop OS. And you also don’t need to mess with that. It’s because the firewall is on the router.
OP said clearly that this “is just my personal computer” and here we all are spreading unintentional FUD about firewall configs as if it’s for a public-facing server.
This pisses me off a bit because I remember having exactly the same anxiety as OP, to the point of thinking Linux must be incredibly insecure - how does this firewall work? dammit it’s not even turned on!! And then I learned a bit more about networking.
This discussion should have begun with the basics, not the minutiae.
Many people use laptops and use other wifi networks or tether to their phone, both can expose you because of unknown firewall states or IPv6 being used.
Yes, I am one of those people, literally all the time. This is the point of laptops.
And I use default Ubuntu Desktop config, kept up to date of course.
If that makes me and OP sitting targets, then maybe we should address this concern to the people who make distros rather than to a random anxious newbie.
Your phone tether will NAT you and not route any incoming packets that aren’t part of a connection initiated by your host. Firewwll does nothing and anyway you wouldn’t even have any open port inside the LAN unless you run services that open ports.
Its good practice to have a firewall local as well. However, you are right it about it not being to critical
It’s extra management without benefits.
But it also doesn’t matter if you never open any ports.
Since 99.99% of users only consume content with a browser, then a firewall that blocks all incoming connections won’t impact them negatively.
If you really need one take white list approach. Block everything you don’t need and only open what you need. Have fun finding out what you need.
Worth noting that if you’re trying to block telemetery or ads or things like that, using an adblocking dns is probably the better option. Either through a pihole on your network or some online adblocking dns.
Other than that, if you’re looking for one because you think you “need” one, don’t worry too much if it’s just a personal computer connected to a router. Most distros ship with sensible defaults for security.
If you actually want to use a firewall, block all incoming and allow all outgoing is a reasonable rule of thumb if you aren’t running a server. Note that “block incoming” doesn’t block connections that the system itself started.
Blocking incoming traffic and accepting outgoing traffic is usually the default for distributions anyway.
Not unless it is a server distro
Debian is a notable exception.
Not really
This seems to be some of the most worthwhile advice. I do use a pretty reasonable DNS client (NextDNS) and it allows me to configure some useful filters and such, and when I’m browsing the internet I also use uBlock Origin and manually allow any third party content one by one.
I did configure UFW to block incoming and allow outgoing, and that should be more than enough for me. I think I’m a pretty “standard” user in the sense that I would make a fairly average target for a would-be attacker. It’s not like I own a web server with goodies worth exploiting.
A part of me really wants to learn more because at some point I’ll have my own router that I’ll want to ensure is configured properly because I’ll likely end up making my own server for media stuff.
Thank you for your reply!
I recommend reading “TCP/IP Illustrated: Volume 1, Second Edition” if you want to learn more about networking. Make sure it’s the second edition, because the first edition is very old. The second edition is also over a decade old now, but it’s still almost completely correct, as the basics haven’t changed much. And don’t mistake the book to be overly simplified because of the title; it’s a very technical book that references the actual RFCs wherever appropriate.
You should block everything, except the things you want to get through. A firewall (at least in Linux) blocks everything inbound by default.
A firewall (at least in Linux) blocks everything inbound by default.
are you sure? I thought that at least UFW allows through some common LAN services
UFW
This is just my personal computer and I’m a newbie to configure firewalls
Leave it alone.
If you want to experiment, set up a VM and experiment there.
Also, if you want to learn about Linux firewalls, go for iptables instead. UFW is easier, yes, but you won’t get the standard way of configuring a Linux firewall, though to be honest, unless you are directly connecting the computer to the internet, you probably won’t need to bother.
And if you are working in an environment where you are dealing with a segmented network with limited access between segments, they will probably already use a separate firewall that is easier to manage centrally than induvidual firewalls running on individual computers
deleted by creator
I think it’s fine to start with UFW on a desktop system at home to learn the very basics and get an idea on what ports you actually need. learning iptables/nftables is useful, but not necessary for a simple user at that level
Eh, I get what you mean but I disagree.
That is sort of saying that if someone want to learn Swedish, but since they don’t know any Swedish, it is better to start them on Norweigan first.
If UFW had used a similar syntax to that of iptables, then it would be a decent way of doing it, but in this example I disagree with you
That is sort of saying that if someone want to learn Swedish, but since they don’t know any Swedish, it is better to start them on Norweigan first.
nobody wants to learn Swedish here. they want to be understood in a community that knows both Swedish and Norwegian, and if Norwegian is easier, they can learn just that
If UFW had used a similar syntax to that of iptables, then
then it wouldn’t be Uncomplicated anymore
No one uses IPtables as a Firewall. That would be insane. Instead you set Firewall rules which then translate to IPtables under the hood
What can I do to see the intetnet traffic from individual apps
what I might want to block?
One strategy is to block everything, and open ports as needed. Beware that most guides focus on inbound traffic, whereas you seem to be focusing on outbound traffic.
wireshark does not work for individual apps, it cannot make a difference between traffic of process a and b.
I’m not sure how Wireshark is related to firewalls honestly. It is mostly a layer 1 and 2 tool
Why are we recommending Wireshark? That doesn’t make any sense what so ever. If anything have them run a port scan with nmap.
This is crazy advise
A firewall by default blocks everything coming from outside going in (without being requested).
Firewalls can also block traffic going out from your PC to the internet. In a company where you need to protect against data exfiltration by employees, and as a last resort safeguard against malware communicating with outside servers, you want that. In that case, a security expert makes a detailed plan of all installed software, to determine what needs to connect from which internal IP to which external IP over which port. Then all other outbound traffic is blocked. This needs to be adjusted constantly, every time a new software is installed or an update changes a software’s requirements. It’s a full-time job.On a home PC running Linux, that’s absolute overkill. There are no untrusted users in your home and you’re probably not the target for a directed attack by skilled actors. So just leave ufw on default, which blocks all inbound traffic and allows all outbound.
I think you might be looking for something like OpenSnitch.
In a nutshell,
-
Use wireshark
-
See if theres any weird connections going on (i.e you visit pancakes.com and wireshark shows unrelatedsite.com making a request as well)
-
Block unrelatedsite.com
“What about firewalls?”
Block from ports 1000 'till the very end (65565 if I’m not mistaken.) – that is your “bread and butter” approach.
“W-what if I’m using a port past 1000?”
Nah, you (very likely) aren’t and never will.
Don’t listen to this guy at all.
This is not great advise to say the least. You want to block all incoming but allow all outgoing.
Also visiting a https site will not magically ports. It uses 443/tcp and if you are using a site with WebRTC (used for calls on platforms like teams) ports 443/UDP and 50000-65535/UDP. However, there is no reason you need to know that unless you are in a professional field
-
You don’t need a firewall on a typical desktop computer. You only need them on routers and servers.
That is because your personal computer is not actually on the internet. It is on a local network (LAN) and it talks only to your router. The router is the computer connected to the internet, and it has a firewall.
The question highlights a classic misunderstanding about networking that IMO should be better addressed. I was like OP once, and panicking about this pointlessly.
Addendum: You’re all replying to OP as if they’re a sysadmin managing a public-facing server. But OP says clearly that they’re just a beginner on a PC - which will almost certainly be firewalled by their router. We should be encouraging and educating people like this, not terrorizing them about all the risks they’re taking.
I think you need a bit of Swiss cheese in your security philosophy. Relying only on your router’s firewall is a single point of failure. If it fails you are screwed. Relying on multiple layers means if one layer fails, another one might save you.
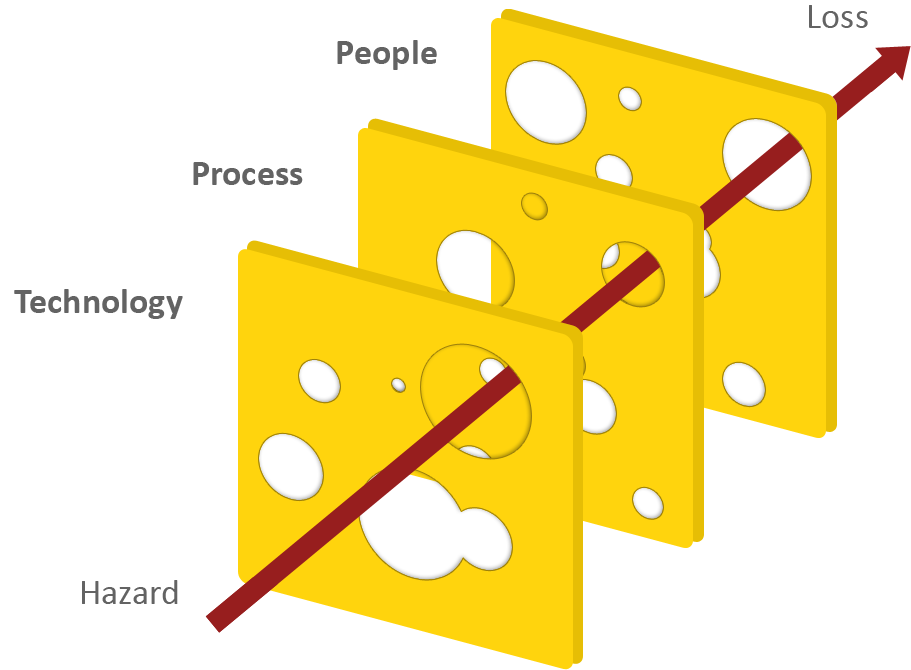
Well, screwed I will be, then. I’m not going to waste my life babysitting a bespoke firewall on my Ubuntu Desktop.
And it seems like a bad idea to be telling beginners on Ubuntu or Mint whatever that their “security philosophy is flawed” and they must imperatively run these 10 lines of mysterious code or else bad things will happen.
This whole discussion looks like a misunderstanding. OP is not a sysadmin on public-facing server. They are a beginner on a laptop at home.
I mostly agree with you, but given it’s a laptop that may not always be at home. It is wise to consider enabling the firewall when connecting to other untrusted networks like Starbucks
Yes, fair point.
As I understand it, the main risk of an untrusted local network is with DNS. The best precaution being to set it manually (to 1.1.1.1 for example or ideally something less centralized). Actually I used to do that myself, running a stub DNS server on localhost. This kind of option really should be in every OS by default.
Would be interested to know the consensus on better locking down a roving laptop.
You don’t understand networking. The local firewall will only stop traffic coming in locally and your average Linux desktop doesn’t have services listening outside of localhost anyway
Unless your ISP provides IPv6 connectivity, which gives every endpoint a globally-routable address. Firewalling at the router only works because of NAT.
That’s why I wrote typical. The question was from a beginner, not a networking expert.
Indeed… IPv6 needs to be actively disabled, not enabled, by default.
the command ss shows connections
I would advise that you ignore a lot if the advise here and do your own research. You probably don’t need a local Firewall and if you want to block content use DNS and browser extensions
You probably don’t need a local Firewall
If the computer never leaves the house, maybe. If it’s ever on public Wi-Fi though, default deny inbound at a bare minimum. Linux computers with cups installed and running but no firewall were revealed yesterday to be vulnerable to RCE.
Cups only listens on local host only by default. Also it requires you to connect to a printer which is unaffected by the Firewall.
You don’t need a firewall on the LAN. It is just an annoyance to have to open ports later. Extra bureaucracy without benefits. This isn’t Windows, you can can easily control your processes, choose if they bind to the network interface and on which port.
Lots of good answers here but I’ll toss in my own “figure out what you need” experience from my first firewall funtime. (Disclaimer: I used nftables – it should be similar to ufw in terms of defaults though).
- Right off the bat, everything unneeded was blocked. I “needed” no configuration, except for maybe…
- Whatever CUPS runs on (when I use it)
- Sometimes I ran
python -m http.server– I unblocked port 8000 for personal use. - I chose to unblock port 53 (DNS). I wanted to connect to another computer via hostname IIRC (e.g. connecting to raspberry-pi.local. I might be misremembering this though).
- At one point I played with NGINX – that’s port 80 (HTTP) and port 443 (HTTPS).
- SSH was already permitted (port 22 – you need root access to enable traffic through ports below 1024 anyway so this wasn’t an issue for running typical apps)
I didn’t use WireShark back then, really. I think I just ran something like
sudo lsof -nP -iTCP -sTCP:LISTENwhich showed me a bunch of port traffic (mostly just harmless language servers).
You don’t have to dive to deep into all the “egress” and “ingress” and whatnot unless you’re doing something special. Or your software uses a weird port. (LocalSend lol)








